So there I was one fine evening, connecting to the internet, sending DHCP request packets to the local DHCP server for address allocation, when I noticed I wasn't getting any IP allocated to me. Some problem with the DHCP.
I 'pinged' the DHCP server thinking that it might be down for some reason. But it did send me a reply, so it was up. Then why wasn't it allocating an address to my computer?
Someone over the LAN had recently discovered Yersinia and proceeded to carry out a denial of service attack on our local DHCP. Not cool.
I decided to write up on Yersinia, since it makes DOS attack on DHCP quite simple and easy with its GUI.
If you're using Kali Linux, type:
#yersinia -G
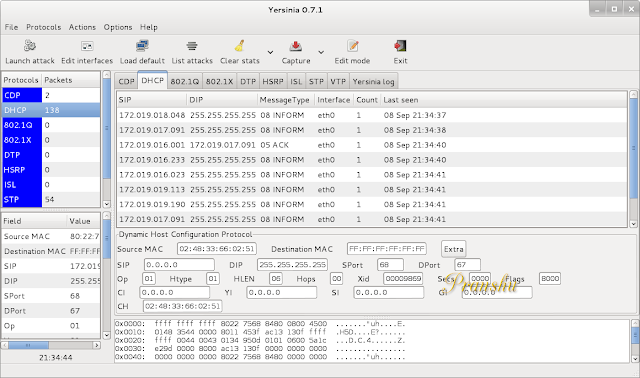
This will bring up the GUI which looks like this:
A super-quick discussion on DHCP, this is what happens on the network:
- I got No IP - You power up your machine. It doesn't have an IP.
- DHCP DISCOVER: Where can I get an IP? - If configuration isn't set to static, your machine looks for active DHCP servers in vicinity to get Configuration Info.
- DHCP OFFER: I can give you an IP - The packets from your machines get to the local DHCP server and it sends DHCP offer to your machine.
- DHCP REQUEST: Great!! Tell me my IP - Your machine responds by requesting configuration.
- IP Allocation - DHCP Server selects an IP address from its 'pool' of free IPs and allocates it to your machine's MAC address.
So the concept is to send many DHCP discover packets to the local DHCP server, using a different spoofed MAC address each time. The DHCP server's free IP pool would quickly exhaust and a genuine request for DHCP would go unsatisfied.
So here's how we send many DHCP discover packets through Yersinia:
In my Case, I noticed within seconds that '163903' packets were sent. This is a DOS attack on the DHCP server.
Finally, you can stop the attack by 'list all attacks' and then cancelling the active attack.
You can find a 'yersinia.log' file created in your 'home' directory after the attack.



It happens only when you use a static IP rather than dynamic one.Dynamic IP keeps on changing from time to time to remove the possibility of errors.
ReplyDeleteThanks
Silvester Norman
Change MAC Address