This post is meant to simplify the procedure for generating GNUPG keys on a Linux machine. In the example below, I am generating a 4096 bit RSA public private key pair.
Step 1. Initiate the generation process
#gpg --gen-keyThis initiates the generation process. You have to answer some questions to configure the needed key size and your details. For example, select from several kinds of keys available. If you do not know which one you need, the default 1 will do fine.
I usually select my key size to be 4096 bits which is quite strong. You can do the same or select a lower bit size. Next, select an expiration date for your key -- I chose 'never'.
Step 2. Generate entropy
The program needs entropy, also known as randomness, to generate the keys. For this you need to type on the keyboard or move the mouse pointer or use disk. However, you may still have to wait a while before the keys are generated.
For this reason, I use rng-tools to generate randomness. First install 'rng-tools' by typing:
#apt-get install rng-toolsRun the tool:
#rngd -r /dev/urandomThe process of finding entropy should now conclude faster. On my system, it was almost instantaneous.
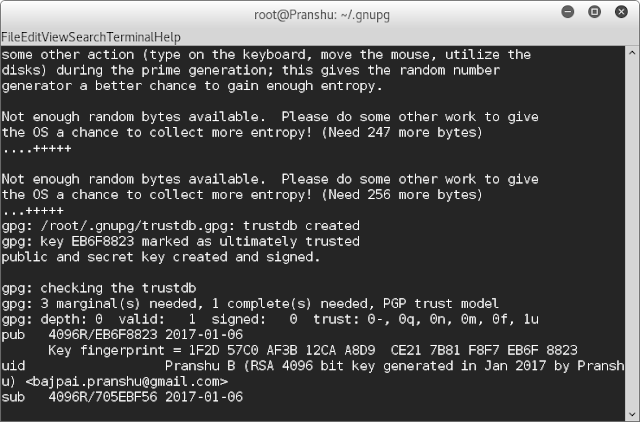
Step 3. Check ~/.gnupg to locate the keys
Once the keys are generated, they are usually stored in ~/.gnupg, a hidden gnupg directory in the home folder. You can check the location of keys by typing:#gpg -kThe key fingerprint can be obtained by:
#gpg --fingerprint
Step 4. Export the public key to be shared with others
For others to be able to communicate with you, you need to share you public key. So move to the ~/.gnupg folder and export the public key:
#gpg --armor --export email@host.com > pub_key.asc'ls' should now show you a new file in the folder called 'pub_key.asc'. 'cat' will show you that this is the public key file.
Important !
Needless to say, do not share your private key with anyone.




No comments:
Post a Comment